DevSecOps beyond the buzzword: shift security left without slowing the business

Spoiler: DevSecOps doesn’t “fix things for everyone.” It architects processes that make everyone responsible—and fast.
A short true story (you might have lived it)
Release day. Your CI/CD hums along: merge, build, test, staging deploy. All green—until the security audit lands. The report lights up: vulnerable library, plaintext secrets in code, an unhardened container image, a Kubernetes pod with excessive privileges. The release halts. Hours turn into days. Meanwhile, new versions pile up behind the audit gate. Your sleek DevOps flow stalls at the very end.
That’s not bad luck—it’s a process anti-pattern caused by treating security as an endgame check. The remedy? Shift it left and weave it into the flow, not tack it on at the end.
Why security is truly multi-layer now
We no longer ship monoliths: microservices, APIs everywhere, external services, containers, Kubernetes, often in the cloud. Each layer expands the attack surface: app, runtime, pipeline, infrastructure. Your security posture is the real state (not the assumed one) of this stack. DevSecOps exists to measure that posture, highlight issues, and drive remediation.
Key idea: if security is everywhere, it must be automated everywhere.
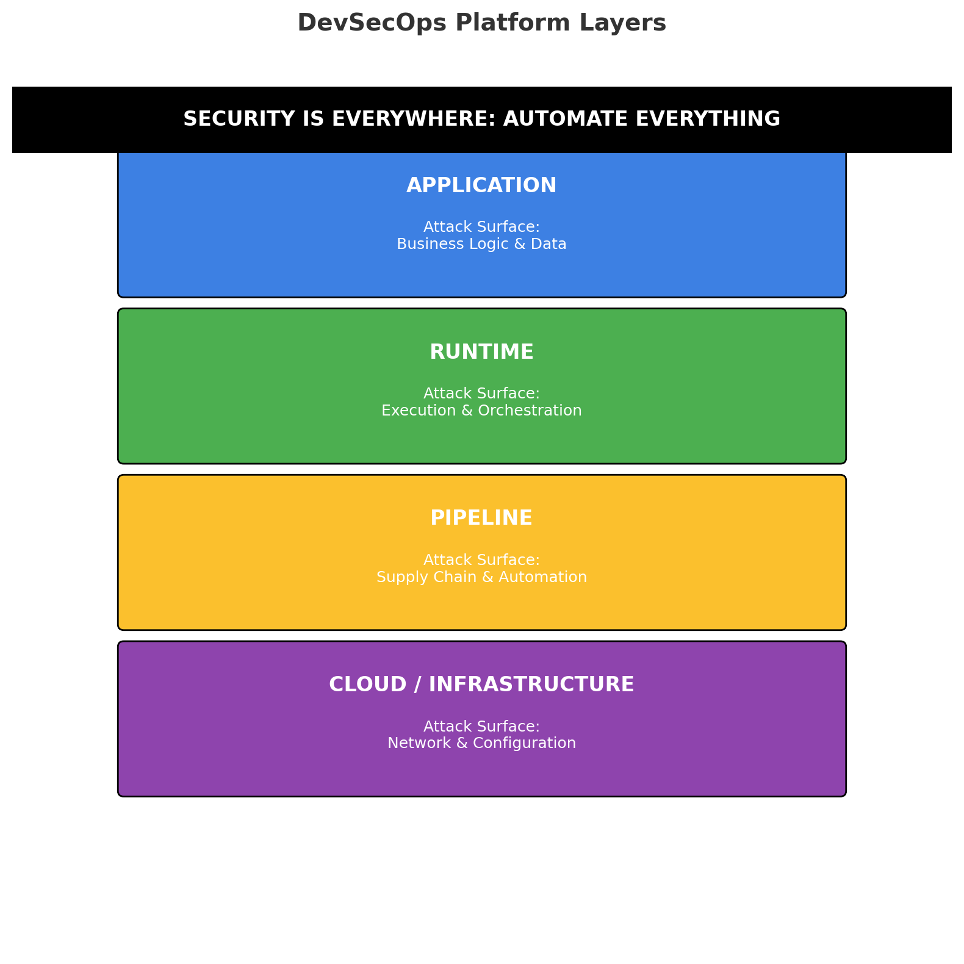
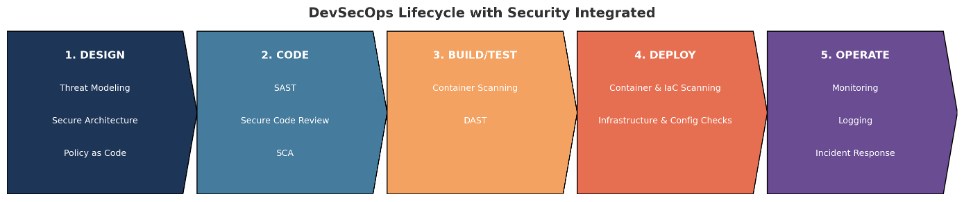
From bottleneck to flow: what “shift-left” really means
“Patch management” (fix later) is expensive and brittle. DevSecOps flips the script: design for security, test earlier, and automate in the CI/CD path with immediate feedback to developers. You fix issues when they’re cheap, and the delivery loop stays smooth.
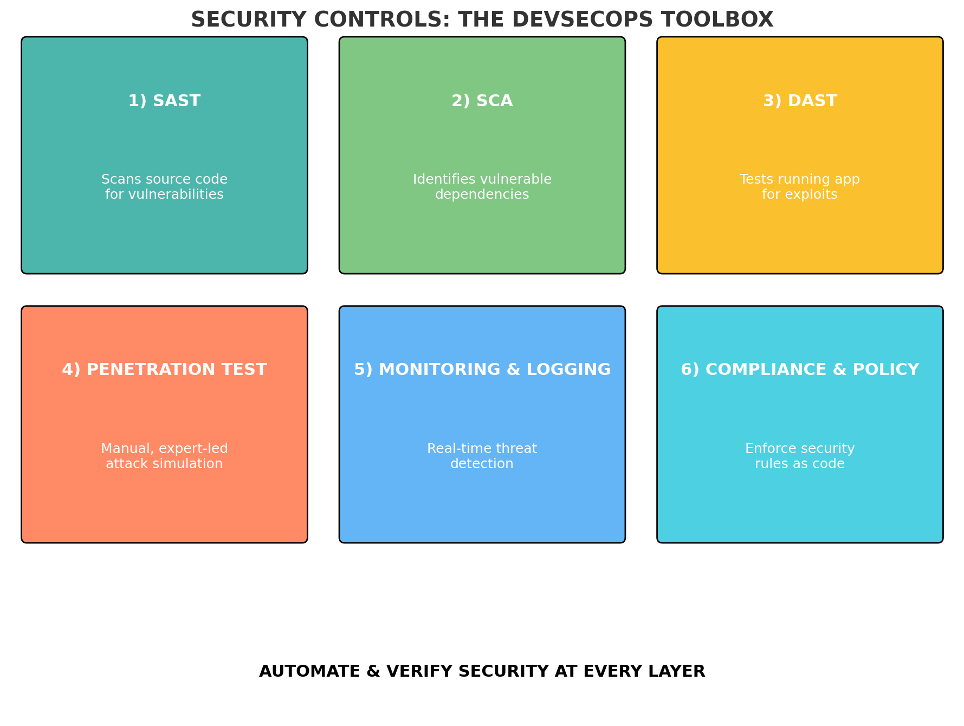
The controls that matter (and when to use them)
1 - SAST — Static Application Security Testing
Scans code for insecure patterns: injection, XSS, hardcoded secrets, missing crypto. It’s powerful because it works with just the code, catching mistakes before they become exploits.
2 - SCA — Software Composition Analysis
Parses dependency manifests and checks them against vulnerability databases, blocking builds with known-bad libraries or problematic licenses.
3 - DAST — Dynamic Application Security Testing
Exercises the running app with simulated attacks (black-box). If the attack works, the flaw is real. If you don’t do it, an attacker will.
4 - Beyond automation
- Manual penetration tests for business logic and complex cases (often mandated in regulated industries).
- Continuous logging/monitoring and alerting to catch what slips through tests.
- Compliance & policy as code, container image scanning, and configuration linting for infra.
CI/CD integration without developer backlash
Running everything on every commit slows teams. Balance depth and frequency:
- Fast lane (each push): incremental SAST on diffs, SCA only when deps change, targeted config checks.
- Slow lane (nightly/scheduled): full SAST, deep DAST, full-graph SCA, image & IaC scanning.
You keep feedback fast without sacrificing thoroughness.

Roles & responsibilities: the architect (DevSecOps) and the team
The DevSecOps engineer is not a fixer-of-everything—they’re the architect of security processes. They design pipelines, integrate tools, set policies, visualize results, and enable action. But they don’t fix on behalf of teams: code flaws are on developers; infra issues on ops; security engineers bring deep expertise and design advanced controls. Responsibility is distributed, not centralized.
This process architecture turns security into a daily habit: tools provide educational feedback (“here you risk SQLi”), teams learn, and next time they write safer code. Culture changes because the system trains it every day.
The business case: earlier fixes cost less
Production fixes are costly and risky; blocking a hardcoded API key at commit time is trivial. DevSecOps shortens the feedback loop and reduces average remediation cost per vuln. In a microservices world with frequent releases, that delta often decides whether you’re ahead or behind.

Where to start tomorrow morning
- Map current posture (minimum viable tooling across code, deps, containers, IaC).
- Define fast/slow lanes in CI/CD and automate essentials.
- Set clear policies (blocking vs warning) and tolerance thresholds.
- Visualize results (dashboards) and make them visible to teams.
- Train from real findings: every issue is a learning moment.
- Schedule periodic pen tests and monitor in production.
DevSecOps doesn’t ask you to “do more,” but to do earlier and better. Start small, automate, measure, iterate—until security is part of your flow, not a last-mile roadblock.

